An Nmap Full Connect Scan Uses Which of the Following
Use the following command to run a stealth scan. Nmap is an open-source utility for network discovery.

Penetration Testing And Vulnerability Assessment Enciphers
Half open scanning C.
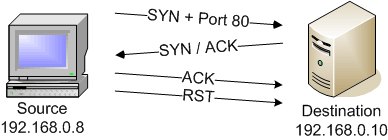
. When you run an Nmap ping scan as root the default is to use the ICMP and ACK methodsNon-root users will use the connect method which attempts to connect to a machine waiting for a response and tearing down the connection as soon as it has been established and thus it will result in a full TCP scan. Which of the following is an example of a passive fingerprinting tool. Which of the following is the Nmap command line switch for a full connect port scan.
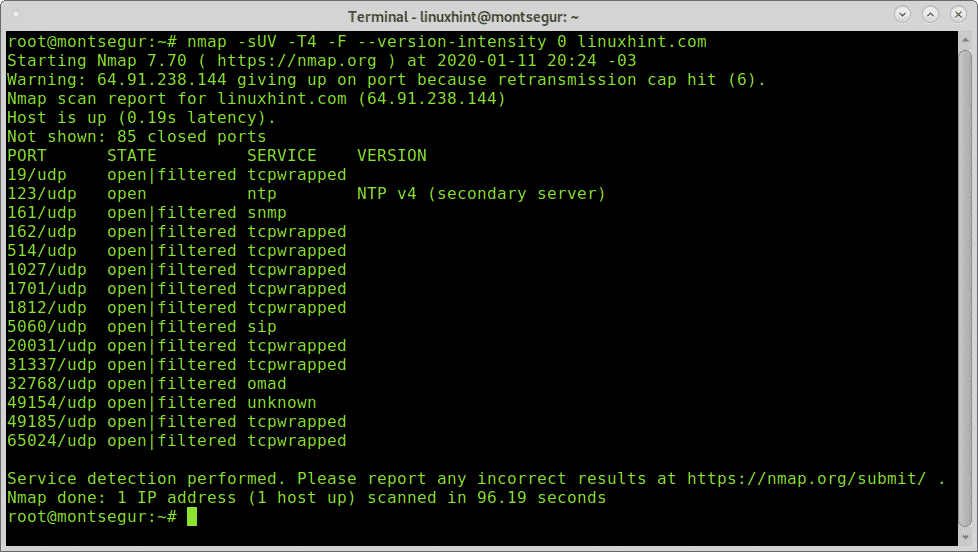
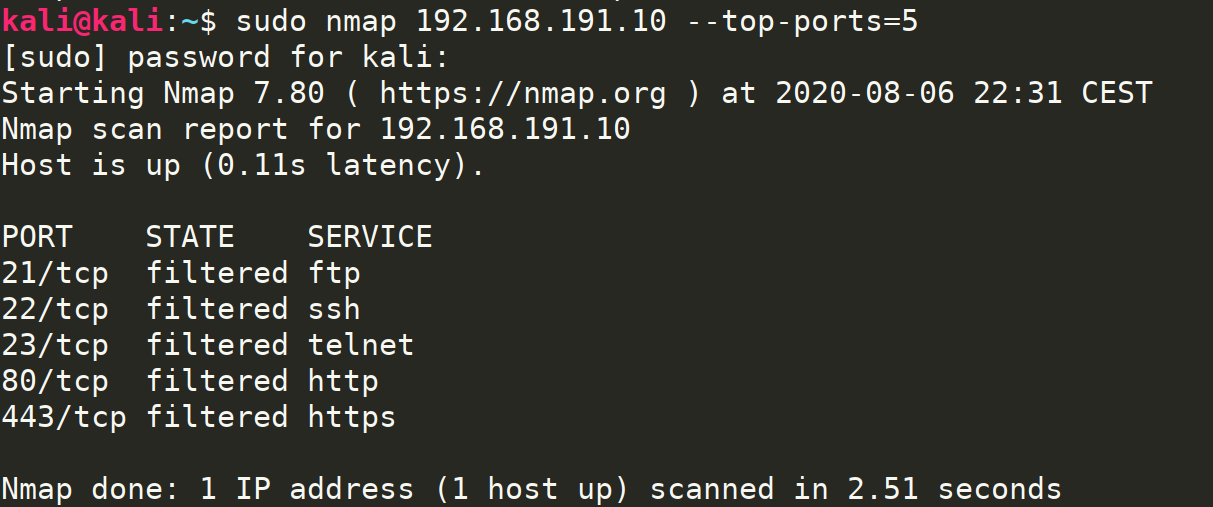
Nmap 1921681110 scan a hostname. Scan Fast the most common ports. We should explicitly specify the UDP protocol for the UDP port scan.
The simple type of Nmap scan where it pings to all the available IP addresses to check which IP addresses respond to ICMP or Internet Control Message protocol is called Ping Sweep. It is used by network administrators to detect the devices currently running on the system and the port number by which the devices are connected. We will use -sU for UDP protocol specification.
You can use the following to execute this Nmap command. If a successful connection is made then Nmap concludes that the port is open. In this type of port scanning technique the scanner sends a request to communicate with the destination server on the desired port.
If the target server is in the. Which of the following is an. If the users need to know only the number of IP addresses and not many details this Ping Sweep is very useful.
To scan all ports 1 65535. TCP and UDP both use flags. See the answer See the.
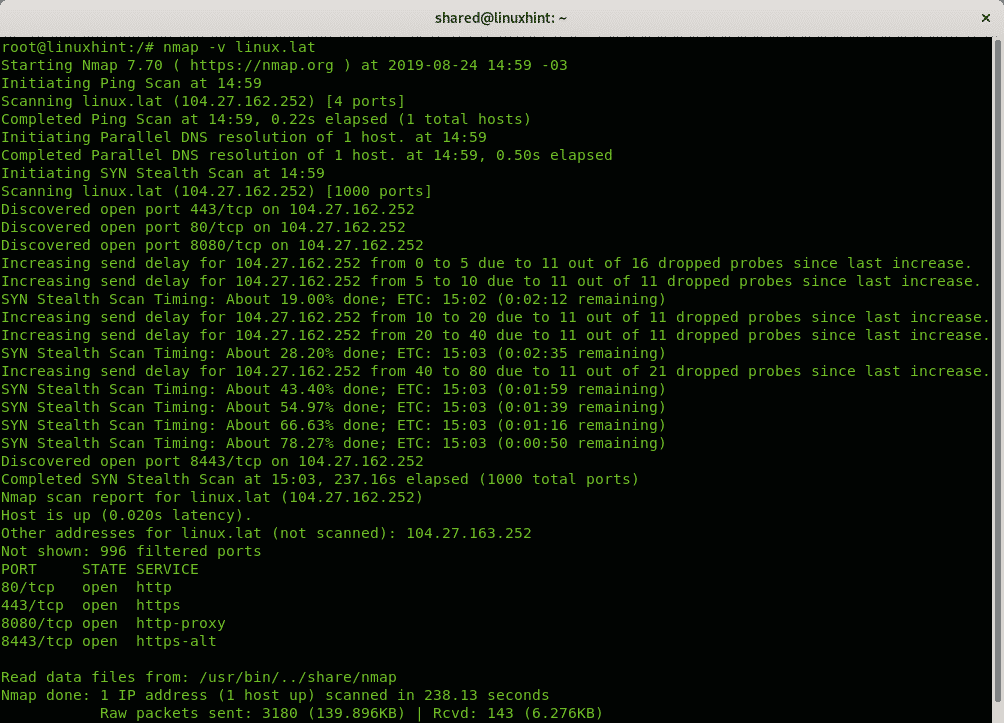
When SYN scan is available it is usually a better choice. The time taken to perform this scan according to. Nmap myhostname Scan a range of IPs in this case from IP 100 to 120.
Give the proper NMAP syntax for the scan type against target 10123 Full Connect Scan Scan Purpose. This request is sent by the TCP Connect scanner system. A connect scan attempt s to make a connection using the UNIX connect program to another host.
Notice that the output is a list of open ports because it is quite reliable with the TCP connect scan. Nmap -sU -p0-65535 1921681221 Scan All UDP Ports. However Nmap supports several more advanced port scanning techniques.
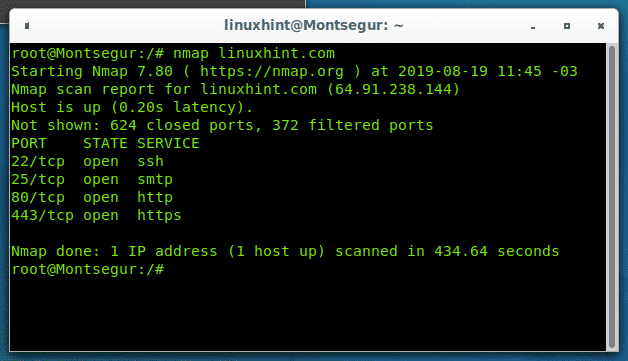
Network Mapper is a security auditing and network scanning independent tool developed by Gordon Lyon. Nmap 1921681100 - 120 nmap scan subnet Scan a subnet. You can use the following commands for scanning a IP address or host on the network.
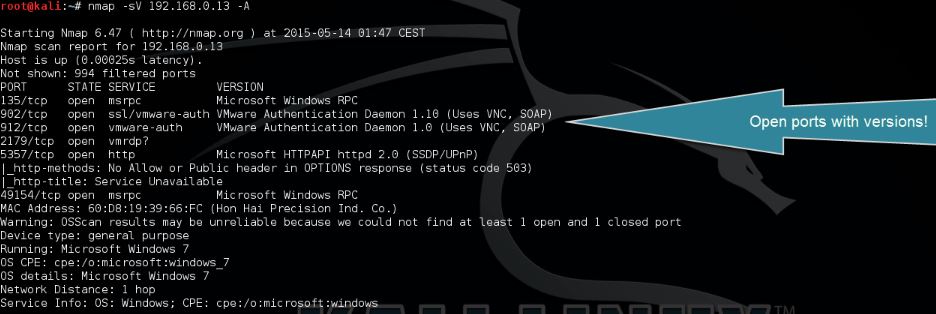
The most reliable type of port scan is TCP TCP Connect Scan or Full Open Scan sometimes known as Vanilla Scan. Nmap -sp 4. 30 pts For each of the following NMAP scan types Full connect Stealth Inverse TCP XMAS Ack probe list.
Nmap p 1-200 19216801. A stealth scan checking all open ports excluding ports 123 and 153. NMAP -sS -O -p 123153 1921681004.
In short if a successful connection is made then Nmap concludes that the. We will use the same port range specification used in TCP. Fill out the following table that defines common NMAP commands.
Nmap p 80 19216801. In the following example we realize a Nmap portscan with tortunnel via proxychains. Sudo nmap -sS -P0 1921681115.
Nmap -p- 1921681221 Scan All UDP Ports with Range. Many systems and network administrators are used for. Perform service and OS detection scan for vulnerabilities and evade firewalls.
If a connection cannot be made then the scan has failed. Scan the Most Popular Ports. Which of the following is the Nmap command line switch for a TCP full connect port scan.
Nmap IP or host Scan Commands. Rather than read raw packet responses off the wire Nmap uses this API to obtain status information on each connection attempt. Nmap 19216810 24.
A stealth scan opening port 123 and 153 A stealth scan determine the operating system and scanning of ports 123 and 153. Nmap scan through the Tor network Configuration. Full connect or TCP connect B.
SYN stealth scan and TCP connect scan. Another common scan is the TCP connect scan. This can be done by using the following.
It is part of a programming interface known as the Berkeley Sockets API. Indeed by default Tor uses a minimum of 3 hops. How to Scan ports using Connect Scan on Nmap.
Nmap also features many tools and options that can be used to do things like. Thanks to tortunnel we directly use a final exit node which makes the scan much faster. Task command syntax TCP full connect scan TCP stealth scan UDP scan Switch to adjust scan time ldle scan switch Decoy switch.
This can come in handy for users who run Nmap on a home server. Not only can we use it to scan every port both TCP and UDP on a computer we can also use it to scan an entire network to try and identify all possible targets. As the name suggests this command auto-scans several most popular ports of a host.
In this recipe we talked about the two default scanning methods used in Nmap. Nmap --top-ports n 1921681106. Scan port 80 on the target system.
The reason why we need tortunnel is that it enables to scan faster. Nmap p 19216801 Other Types of Nmap Port Scans. OS scanning is one of the most powerful features of Nmap.
Nmap has less control over the high level connect call than with raw packets making it less efficient. What will the following nmap command accomplish. In the log files it does not leave any trail.
As mentioned above you can perform a host scan using the following command. Nmap commands can be used to scan a single port or a series of ports. When using this type of scan Nmap sends TCP and UDP packets to a particular port and then analyze its response.
This problem has been solved. Nmap uses TCP as the default protocol for the port scan. Scan ports 1 through 200 on the target system.
Nmap Scan Specific Udp Port Devsday Ru

Scanning Open Ports In Windows Part 3 Nmap
How To Scan Ports Using Connect Scan On Nmap Eldernode Blog
Nmap Open Port Scanning And Os Detection
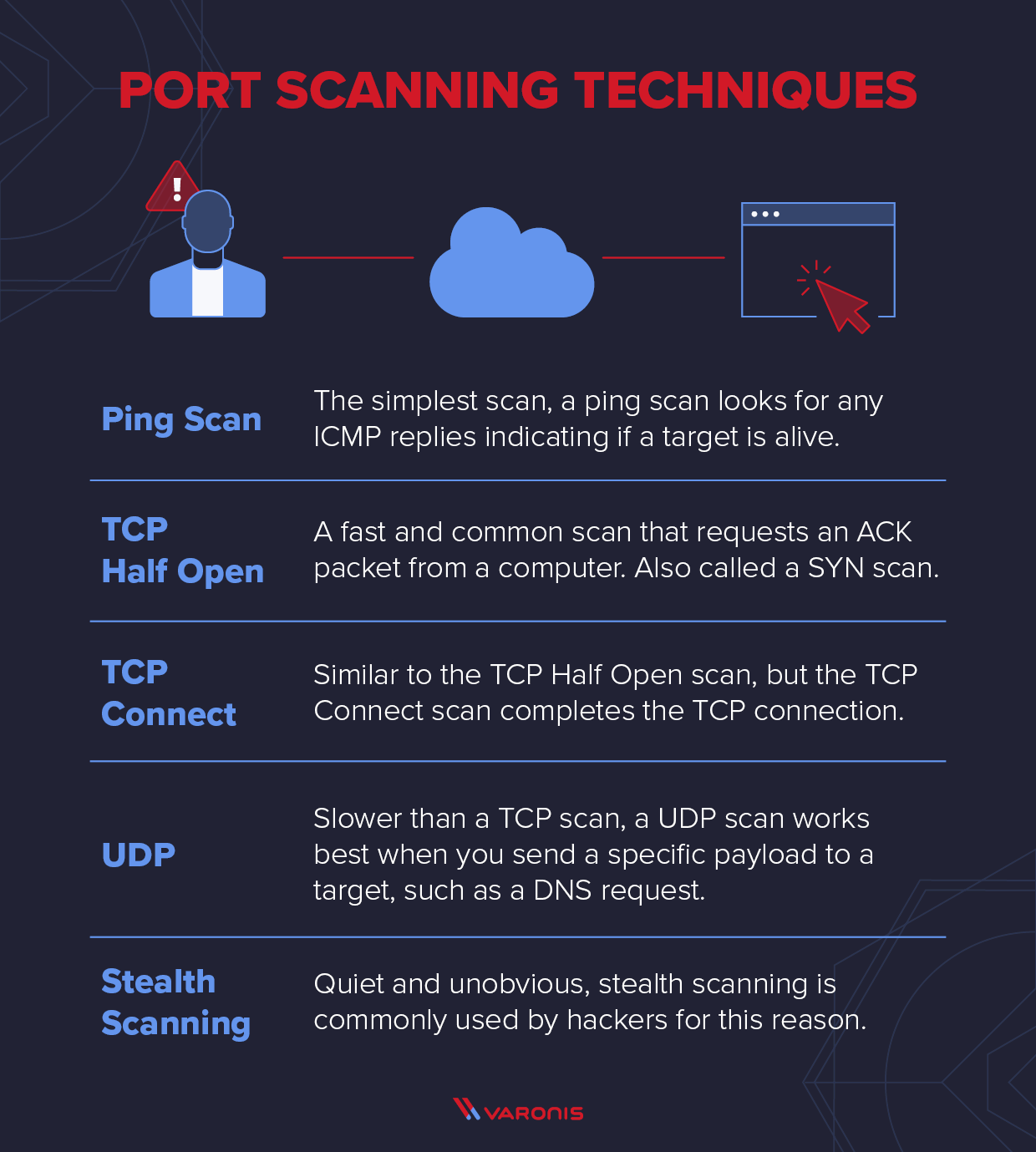
What Is A Port Scanner And How Does It Work

What Is A Port Scanner And How Does It Work
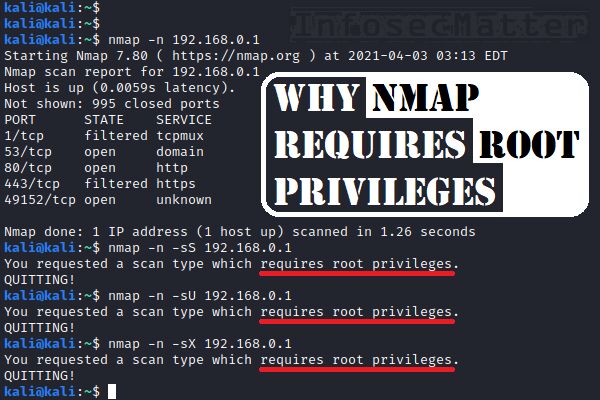
Why Does Nmap Need Root Privileges Infosecmatter
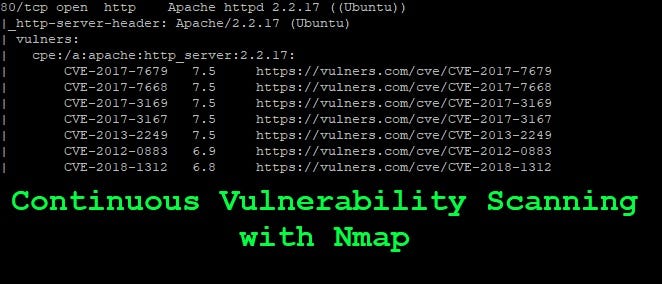
Continuous Vulnerability Scanning With Nmap By Alexander Tyutin Medium
How To Scan Tcp And Udp Ports With Nmap Poftut
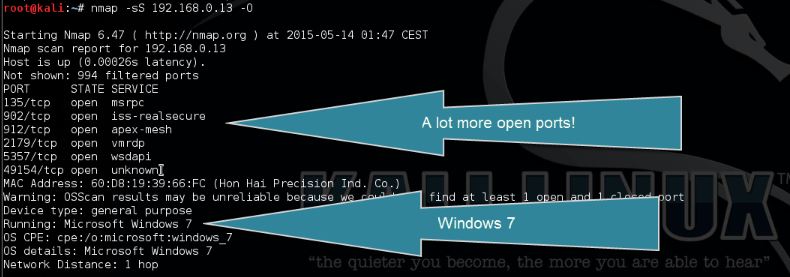
Nmap Open Port Scanning And Os Detection

Inside Nmap The World S Most Famous Port Scanner Pentest Tools Com Blog

Deep Dive Into Nmap Scan Techniques By Pentest Duck Medium
Nmap Pn No Ping Option Analysis By U Y Medium

Nmap Basic Overview On Scanning Techniques

Optimizing Your Nmap Scan Nmap Scanning Methods Professor Messer It Certification Training Courses

Nmap Command Examples For Linux Sys Network Admins Nixcraft

Comments
Post a Comment